Increasing “Jointness” and Reducing Duplication in DoD Intelligence
by Chris Rasmussen
with contributions from LCDR John D. Ismay, John Bordeaux, Bob Gourley, Michael Tanji
This paper was submitted to DoD’s INVEST (Innovation for New Value, Efficiency, and Savings Tomorrow) contest on September 23, 2010.
The explosive intelligence spending over the last decade initiated by the 9/11 attacks has been both a blessing and curse. The initial spending was a warranted blessing but as time passed it turned into a curse that created far too much duplication of effort, fragmentation, and sprawl throughout the United States Intelligence Community (IC). The initial infusion of cash dovetailed with a renewed focus on information sharing and “collaboration,” which was emphasized in the Intelligence Reform and Terrorism Prevention Act (IRTPA) of 2004. While modest gains have been made in breaking down “stovepipes,” the initial energy of these “collaborative” efforts has waned and increased spending has largely cemented bad habits: siloed analytic reporting that fuels massive duplication of effort. If these negative trends continue and a new “joint” business model is not adopted wholesale, the promise that sparked IRTPA is in danger of being unrealized. A move way from the newspaper-like “finished intelligence” model to a “purple intelligence” model more aligned with Internet-enabled global trends in content-centric enterprises will increase analytic “jointness” and reduce duplication–saving billions of dollars and resulting in improved intelligence insight.
Each intelligence agency still behaves much like an independent newspaper writing whatever it wants with limited coordination with other agencies. As newspapers around the world are going bankrupt due to the changes in content creation and delivery of services over the Internet, the Intelligence Community is moving in the opposite direction: more editorial control in the form of “finished intelligence” (vertically vetted projects within an agency) posted to “portals.” This trend ignores the democratizing and crowdsourcing trends of the Internet which are changing the world of personal electronics, software development, consumer spending, content delivery and creation.
The majority of the US Intelligence Community is comprised of Department of Defense (DoD) elements. The “INVEST” ideas expressed in this analysis can be applied to the broader IC, which is beyond DoD control, but the cost saving suggestions of this paper should be applied to DoD elements first to set an example. The term “IC” (Intelligence Community) throughout this paper largely refers to the intelligence agencies of DoD such as DIA, NGA, NSA, the service intelligence elements, and combatant command elements.
Observers of transformation underway in commercial organizations often note that organizations with smaller budgets deliver far greater capability. Many of these small budget commercial capabilities are not only disrupting and shifting markets, but often are delivering capabilities that are more powerful than the legacy systems they displace. Some of the greatest use cases in this area are those observed in the displacement of old-fashioned newspapers for outlets of information. “New” content sources are often of higher quality, greater relevance, and available at much lower costs (almost free!) Since the IC is in dire need of higher quality and more relevance – and all in the federal sector are in need of economical alternatives – lessons from this sector are important to consider.
The literature regarding innovation is clear – technology and process innovation can be put to use as an incremental improvement to existing operations, or can used to disrupt existing operations in pursuit of transformation. One famous case study compares the incorporation of individual online trading technology into the business models of Charles Schwab and Merrill Lynch. Lynch assigned the same brokers, with the same incentive programs, to add online trading to their portfolio. There were no individual incentives to tend to the new channel – and no disruption to the business model was expected or desired. One innovation author notes the contrast with the approach taken by Charles Schwab, which immediately “created a separate business unit to conduct online trading and made a masterful transition to the computer-centric investment management world – ultimately phasing out its original broker-based business unit…the new unit operated at much higher trading volumes and significantly lower costs than those characterizing the traditional business.” The IC cannot continue to marginalize potentially disruptive innovations and hope to thrive in a rapidly changing threat environment.
Intelink and Intellipedia
Intelink, launched in 1994, was an internal governmental response to extend the budding HTML and web browser revolution forming on the Internet to the IC. Websites began to proliferate from PACOM to the CIA to the NSA. In addition to agencies posting “their” content, some agencies started to expose traditional cable traffic – previously bound to dissemination lists – to Intelink for broader discoverability. This could be considered the IC’s “Web 1.0” phase.
In 2005, Intelink started to host a series of “Web 2.0” tools such as wikis, blogs, social bookmarking services, and document storage all of which were indexed by Google Search Appliance. This move was a surprise to many: the stodgy and security conscious IC was moving ahead of many private sector companies with its use of Web 2.0 tools behind the firewall (dubbed “Enterprise 2.0”) to increase knowledge transfer and information sharing. The flagship application in Intelink’s tool kit was Intellipedia—a wiki built upon the same software that drives Wikipedia hosted on all three security networks: JWICS, SIPRNET, and NIPRNET.
Intellipedia is a media darling. The underlying message in the press was “if the IC can use a wiki, so can our company.” Intellipedia and other Intelink 2.0 tools have impressive registration and activity rates and inspired many throughout industry, government, and academia to pursue the “wiki way.” After almost five years of “collaboration” as an industry leader, it is long past time to consider the result. Intellipedia boasts many collaborative successes by facilitating insights among analysts, but this is marginal change. The underlying assumptions regarding the prevailing finished intelligence workflow have not been questioned. In fact, much of Intellipedia’s “success” is rooted in transforming non-analytic work.
Intellipedia has proven effective at reducing the amount of email and streamlining basic administrative work common across the corporate world. Posting office and administrative content (such as concept of operation documents, requirements lists, software design de-bugging matrices, and meeting minutes) to Intellipedia is helpful, but it fails to reach the core function of the IC. The IC’s core business function is analytic output, to date unchanged by this information sharing “revolution.”
Let’s assume that every “enabler” office within an agency (such as human resources, IT, investment, legal, acquisition, logistics, training, etc.) achieves transparent office status, thereby reaping the benefits of crowdsourcing and data discovery, while the analytic core of the agency does not? The result is limited transformation: the primary function of an intelligence unit is analytic output and all “enabler” functions exist to support analysis. The “revolution” is incomplete.
From the perspective of structural analytic transformation, “2.0” tools have done little to reform the approach to analytic “production.” The analytic core is trying to use the “new web” to tell stories in a different way but is falling short for two primary reasons: 1) The “2.0” tools still remain as a complement—not an alternative—to the existing production processes used to create the 50,000 products a year published across the IC and rising. 2) A vast amount of stock content is pushed out in traditional dissemination channels with much overlap. Some have argued Intellipedia is a “knowledge base.” If it is a knowledge base then finding links to base knowledge in “official” or “tailored” content should be easy. It is not. In fact, there are very few links to Intellipedia in official agency output – because it’s not “officially” trusted.
A-Space
Launched in 2007, A-Space is a virtual work environment where analysts connect with other analysts, ask questions, and see what their colleagues are doing. The result is similar to Facebook’s news feed. A-Space is a good place to “think out loud” and ask questions in threaded forums but as Intellipedia before it A-Space is struggling because it doesn’t address reforming or replacing the finished intelligence process.
Patrick Neary, former Deputy ADDNI for Strategy, Plans & Policy, noted: “Analytic Transformation (AT) has as its tag line ‘unleashing the potential of a community of analysts.’ While each of [its] initiatives will—if and when they are successfully deployed—improve the daily routine of community analysts, it is entirely unclear when a transformation in analysis will occur. While the AT initiatives are necessary preconditions to analytic reform, they do not address the decentralized management of analysis or the product-centric analytic process. Real reform in analysis will require agencies to give up proprietary products and share customer relationships, establish new rules facilitating on-line collaboration, and focus more on intelligence as a service than a product.”
The decentralized management of analysis manifests itself in many ways, but the most glaring is that agencies can write “products” on any topic with limited to no coordination with other agencies. They then disseminate those products to their “customers” often without the benefits of “upstream,” joint collaboration. This practice creates incredible amounts of overlap and duplication. The gusher of intelligence spending increased duplication because it simply augmented the siloed habits of analytic production.
The Washington Post series “Top Secret America” revealed: “Many security and intelligence agencies do the same work, creating redundancy and waste. For example, 51 federal organizations and military commands, operating in 15 U.S. cities, track the flow of money to and from terrorist networks.” Many in the IC argue that the “Top Secret America” series was sensationalist and some parts of the story were inaccurate, which is true. However, the observation above is accurate and is a microcosm of the larger problem of excessive duplication fueled by increased spending.
As with most public sector organizations, the application of private sector insights must be tempered by the understanding that private sector goals of efficiency will not always apply. The IC is not designed for efficiency. It’s designed instead to be effective with purposeful overlap built into the system to catch things that may slip by a single entity. A popular saying within the IC is: “one man’s duplication is another man’s competitive analysis.” This axiom is partly true but is too often used to legitimize excessive overlap. For example, five to ten units working the same topic is probably effective but no one can honestly argue that 51 organizations working on the same issue is effective. This inability to scope “sufficient” redundancy leads to uncontrolled costs and a lack of accountability. While efficiency may be sacrificed for effectiveness, this should not translate into rampant task duplication with no cost ceiling or metrics for governance.
Another expression of excessive duplication can be seen in how A-Space is currently being used. A-Space is built around “workspaces” which must be named. Analysts from across community can focus talent and energy on a topic and gain new efficiencies through a combination of “crowdsourced” workflow and the “in-house” work of their team. Unfortunately, this is not really happening. Analysts are projecting the organizational construct of offices, sub-offices and “fusion centers” working similar issues into the potentially “flat” A-Space. For example, there are over 100 workspaces dedicated to Iran. A workspace simply named “Iran” is too generic and more specific workspaces such as “Iran’s Conventional Military” are needed to manage the workflow. But, as previously noted, 25 workspaces devoted to Iranian topics would probably be effective but no one can honestly argue that over 100 is generating synergy.
Goldwater-Nichols Analogy
Many have commented that the IC needs to model the Goldwater-Nichols Act of 1986 to create more “jointness.” Prior to Goldwater-Nichols each military service “trained, acquired, and equipped” and also conducted operations virtually independently. Goldwater-Nichols took war planning and operational powers away from the military services and centralized it to a “commander” of a geographic or functional command. Goldwater-Nichols did several other things: it made the Chairman of Joint Chiefs of Staff the primary military advisor to the President replacing the confusion that resulted when each service chief gave disparate advice. Also, it mandated that flag officers serve in a joint duty assignment in order to receive further promotion. These stipulations of Goldwater-Nichols are outside the scope of this paper but I’d like to focus on the services losing operational power and apply it to the IC.
Goldwater-Nichols created jointness in the military because the services traded off some power to bolster a more effective central entity. The Intelligence Reform and Terrorism Prevention Act of 2004 created the DNI and set in motion many reforms but it did not stipulate that intelligence agencies would have to trade off any power to bolster a command or center like Goldwater-Nichols. The agencies “train, acquire, and equip” but also conduct operations independently much as the military services did prior to Goldwater-Nichols. For the most part, the IC does not conduct kinetic operations like the military, rather the IC’s “operations” are its analytic and collection functions. Some argue something similar to Goldwater-Nichols cannot work in the IC because it’s spread across five cabinet departments unlike the military services which are all under DoD. There is some merit to this argument from a command and budgeting perspective, but this does not detract from the overall message: achieving analytic jointness and reducing duplication with a series of DoD Directives – specifically aimed at removing some of the independent analytic power of agencies, service components, and combatant commands.
Balancing the corporate voice with crowdsourcing
No single agency recognizes any of the content in Intellipedia or A-Space to be “official.” In fact, most of the interaction and content in these social tools is described as “good for collaboration but not the product.” The IC’s product-centric view of intelligence is at the heart of the analytic transformation problem and most “solutions” simply treat various symptoms. If each agency uses “2.0” tools to “coordinate,” but the content creation power lies independently within the finished intelligence process, the analytic transformation movement has gone as far as it’s going to go.
The main objections to Intellipedia and A-Space as “official” sources are that both spaces are too uncontrolled and there is difficulty determining which content “speaks for the agency” within individualized social media platforms. The “agency voice” in finished production is trusted to address issues of accountability, vetting, and records management. Some of these virtues are over-stated in the current system where slapping an agency or command logo on a report imbues the product as being more trustworthy and accountable than any social software-based content. Nonetheless, the IC’s obsession with agency logos is here to stay so a compromise was struck.
A move toward joint production
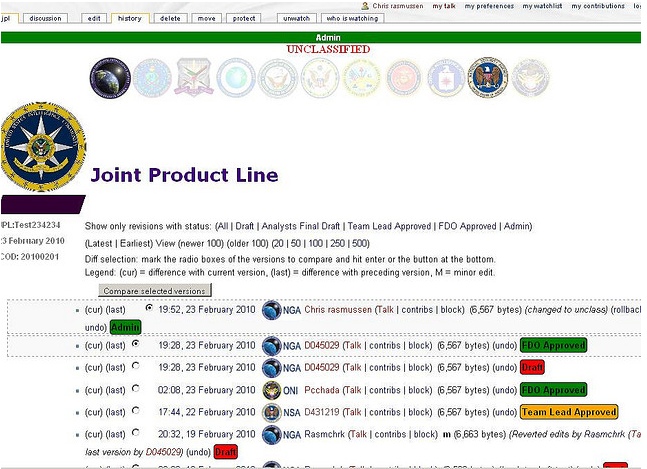
Like Intellipedia, Intellipublia’s Joint Product Line (JPL) is a wiki, but it also includes a built-in approval process and balances crowdsourced content with the agency voice. Readers can see who contributed to an article, which managers approved it, and when those activities took place.
The JPL combines official agency review with emergent content for joint or “purple” output. Users can consume and compare “authorized” versions to the emergent “living” version. Agency logos quickly denote that official vetters have reviewed the content but anyone can contribute and the article cannot be locked down. In addition to agency logos, the “authority” and roles of vetters are denoted by color-coded stamps such as “team leader” and “final authority.” Once the official vetters sign off on the content, their agency logo will become un-ghosted at the top. Ghosted logos show that someone from that agency has made edits but doesn’t have a higher vetting function. This is modified MediaWiki software and shown in the edit history mode. This software is a starting point and needs to evolve, but it’s a strong starting point because the underlying business process (not the technology per se) creates jointness and exposes duplication.
source: http://www.flickr.com/photos/97111850@N00/4390235472
MIT business professor Andrew McAfee stated that “if you want to control the outcome, you need to control the process.” Currently, each agency, command, and fusion center controls every process associated with production and can conduct each process in a vacuum. There is no requirement to coordinate across these organizations. A DoD Directive moving some production power into the JPL network would be similar in effect and benefit to the removal of the operational and war planning powers of the military service in Goldwater-Nichols. The transparent JPL network would now “control” the analytic process. Agencies would no longer have to write using their internal, opaque systems but would would still “control” their agency’s voice – but now without locking down or “owning” every part of the process.
Transferring some analytic production away from finished intelligence posted to agency portals and cable traffic would expose the amount of duplication in the system through transparency and customer feedback loops. There will always be a need for “tailored” intelligence but tailored snapshots should be the exception not the rule and “products” should be the by-product of the collaborative process not the end state. There will always be a need for some duplication but, as previously stated, the amount of duplication is over-kill on most topics. At the limit, the IC needs an approach to understand and be held accountable for the amount and areas of duplication. Moreover, we need to re-examine what “tailoring” means in a smart phone apps and wiki world.
Reforming acquisition and shutting down intel shops
DoD’s fragmented IT acquisition process leads often to excessive duplication and waste. Every agency and command can acquire any technology in a vacuum. More times than not that specific technology often already exists somewhere else. “Not invented here” syndrome and the belief that “our data and requirements are unique” are simply over-stated default assumptions fueling waste across budgets. A-Space, C-Space (for collectors), J-Space (for non-analytic staff workers), Intellipedia, Sharepoint, Army Knowledge Online, Air Force Knowledge Online, Apps for the Army, etc. all provide some niche but most of these systems do similar things. Once again, we are not advocating for total acquisition centralization nor are we suggesting that one purple production system fits all needs. However, if production were centrally “managed” via a transparent system like the JPL we could start to see the excessive duplication of analytic effort and associated IT acquisition. If nothing else, this approach will provide the leadership with visibility into the amount of duplication by topic area.
Once duplication is exposed we can start to roll it up by shutting down unnecessary fusion centers, red cells, and analytic units. The people affected by these cuts can be re-trained or transferred but cutting billets and contracts is absolutely necessary. The HR, facility overhead, engineering, maintenance, electricity, and security costs associated with excessive analytic duplication are unwarranted and wasteful. Moving some of the production power away from the agencies to a transparent and purple network will improve the quality of analytic insight, increase jointness, reduce duplication, and will save billions of dollars. Efficiency that leads to greater effectiveness – a business principle within reach.

 Some firms (and Agencies!) went a bit far. I am still haunted by the story of the Senior Executive at the Department of Defense who saw his secretary replaced by a computer. The professional assistant who knew why papers were filed a certain way, who knew the history for those files, and who maintained an informal network among other assistants that provided the best intelligence operation in existence. Shunted aside (Or kicked upstairs so she could print out some SES's email) because some Executives now had new, mystical, magical machines that would connect the human to all the information he could ever need. This is an example of transforming the office ad absurdum.
Some firms (and Agencies!) went a bit far. I am still haunted by the story of the Senior Executive at the Department of Defense who saw his secretary replaced by a computer. The professional assistant who knew why papers were filed a certain way, who knew the history for those files, and who maintained an informal network among other assistants that provided the best intelligence operation in existence. Shunted aside (Or kicked upstairs so she could print out some SES's email) because some Executives now had new, mystical, magical machines that would connect the human to all the information he could ever need. This is an example of transforming the office ad absurdum.
 It was here I was privileged and sobered to witness the death of Knowledge Management in DoD.
It was here I was privileged and sobered to witness the death of Knowledge Management in DoD.
